Medical device cloud security — protecting data
Protecting medical device data in the cloud
Are you prepared for the shared responsibility of cloud security?
Building cloud-based data collection for medical devices requires technical proficiency to make it work, and regulatory expertise to ensure clinical trial success and FDA clearance. A critical third factor is often overlooked: security to protect the data in the cloud. It is important to understand the distinction between providing security of the cloud infrastructure versus ensuring security in the cloud, i.e., the platform performing data collection, display analytics, reporting, and a host of other functions.
Cloud Security is a “Shared” Responsibility
Public cloud infrastructure providers (AWS, Google Cloud, Azure, etc.) use a “shared” security model in which they are responsible for security at the physical level to prevent unauthorized hardware access. The remaining security objectives are the responsibility of the medical device company.
Cloud providers who offer additional services such as Database as a Service hold slightly more responsibility in maintaining security, though it is still not a comprehensive solution. See, for example, the AWS shared responsibility diagram. Security of the cloud platform including both data in transit and data at rest — as well as access to the data in all phases — is the responsibility of the customer.
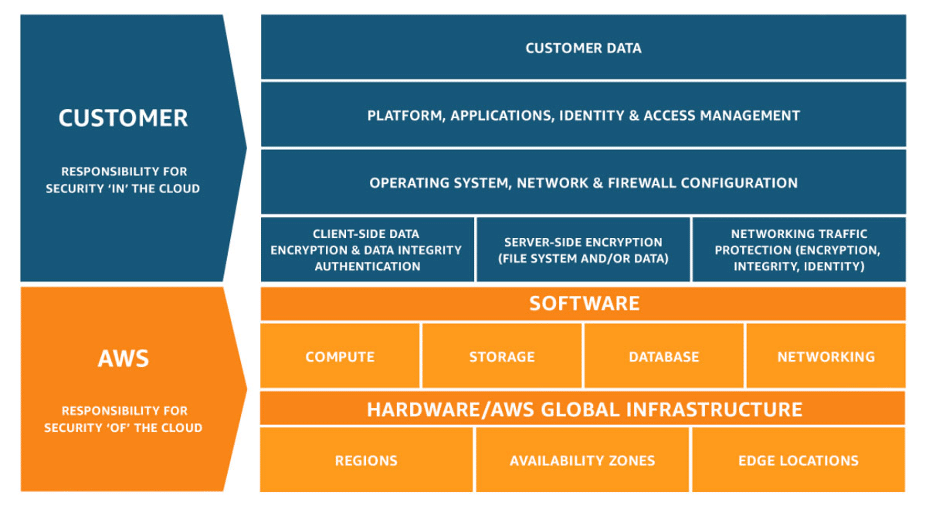
Source: https://aws.amazon.com/compliance/shared-responsibility-model/
Many Companies Using Cloud Connectivity are not Fully Prepared
A close look at the vulnerabilities resulting from ignoring an integrated infrastructure and platform security strategy reveals alarming information. Recent statistics regarding cloud security indicate a general state of vulnerability and cloud security unpreparedness.
- Sophos recently surveyed over 3,500 IT managers globally and found within their organizations:
- 70% suffered a security incident hosting data in a public cloud
- 44% considered data loss or leakage as a top security fear
- 66% have misconfigured cloud services, creating a vulnerability by leaving back doors open
- DSM supports these concerns:
- 66% of IT professionals list cloud security as their number one concern in implementing an enterprise cloud computing strategy
- More than 95% of cloud security incidents are caused by the user — as opposed to the cloud provider
- A mere 12% of global IT organizations fully grasp the effect of GDPR on cloud computing and data storage
- CyberTalk adds to this alarming perspective:
- Almost 80% of organizations recently experienced a cloud security breach
- Of those, 43% endured at least 10 breaches
- While 67% were worried about incorrect security configurations of their cloud production platform
Cloud Platform Security is Complex
Let’s explore the details of cloud platform security.
Security in a cloud platform requires multiple sets of configurations. Each is complex, requiring a combination of information technology expertise, cybersecurity knowledge, and operations planning and execution. The security considerations and how they are addressed within the Galen Cloud™ medical device connectivity platform are described in the following table.
| Security Consideration | Existing Galen Cloud™ Implementation | |
| Identity and Access Management | · Authentication of users, device, and systems
· Authorization so users access only appropriate information |
· Two-factor user authentication
· Machine-to-machine authentication schemes using: OAuth 2.0 Client Credential Grant · Robust user roles with configurable levels of access |
| Network Security | · Restricted access to servers, systems, and services via network and firewall configuration | · Isolation of servers comprising the Galen Cloud™ stack ensures minimal access necessary for each server’s role |
| Data Encryption | · Encryption of data at rest and in transit with the appropriate set of ciphers | · Data encrypted at rest (AES-256) and in transit (AES-128 GCM) |
| Operating Systems Configuration | · Lockdown of non-required services; running service under non-privileged mode; OS patches | · OS lockdown strategy fully implemented
· Regular operating system patching performed |
| Incident Detection and Response | · Constant monitoring of network traffic and access patterns to detect a potential incident, incident investigation, system isolation, system recovery, and providing response compliant with global laws and regulations | · Active security monitoring of underlying infrastructure using industry-standard tools
· Galen Data’s Data Processing Agreement ensures GDPR compliance |
| Redundancy, Availability and Disaster Recovery | · Ensuring systems are up and running with variable load, infrastructure outage, data backups, and systems configuration management to allow for disaster recovery | · All processes routinely audited
· Operational resources (e.g., backup/restore) frequently validated |
| Regulatory Requirements (HIPAA, GDPR, CCPA, FDA, etc.) | · Securing protected data, consent management | · ISO 13485:2016 certified
· Compliant with 21 CFR Parts 11 and 820, IEC 62304, ISO 14971 · Compliant with HIPAA, GDPR, CCPA |
| Software Components (Software Bill of Materials) Vulnerability Tracking and Patches | · Tracking and patching vulnerabilities in components used in the software applications | · Internal and external penetration testing
· Regular system security patching performed |
Buy versus Build
The temptation to build a custom medical device cloud platform stems from several understandable factors:
- A desire to fully customize functionality
- The comfort of direct control of data
- The perception of cost savings (often neglecting long-term maintenance costs)
- A perception that adequate security is supported by the cloud infrastructure provider (“AWS enables HIPAA-compliance, so I’m safe – right?”)
While it is possible to assemble the required expertise to address the security considerations outlined in the table above (technical, regulatory, quality, security, privacy), it is often more cost effective to leverage an existing platform. Such a platform already incorporates a robust set of protections specifically designed for medical device data (PHI, PII, etc.), thereby eliminating a majority of cloud security risk at a fraction of the cost of developing a custom solution.
Galen Data provides the ability to collect, store, analyze, and monetize data in its secure and compliant Galen Cloud™ platform to a growing portfolio of connected medical device companies. Our security strategy is proven. We will be happy to discuss whether it meets the needs of your medical device.








